General Setup
Formatting
| Chain | ✅ Import Format | ✅ Export Format |
|---|---|---|
| EVM | Hexadecimal with or without 0x | Hexadecimal without 0x |
| Solana | Base58-encoded private key | Base58-encoded private key |
| Sui | Bech32-encoded private key | Bech32-encoded private key |
Importing Wallet Keys
When importing an existing private key into Dynamic’s TSS-MPC system, we use Shamir Secret Sharing (SSS) to securely split the key into multiple shares. This process:- Takes your existing private key as input
- Uses SSS to split it into either 2 or 3 shares (depending on your configuration)
- Distributes the shares between the relevant parties (user, server, and optionally a backup)
- Securely destroys the original private key
Exporting Wallet Keys
For maximum user control and portability, Dynamic allows users to export their private keys. During export:- The key shares are temporarily recombined on the user’s device using secure MPC
- The private key is constructed client side and provided to the user
When implementing Dynamic in a custom UI, please ensure you are surfacing this flow to your end-users, so that they always maintain control of their wallet.
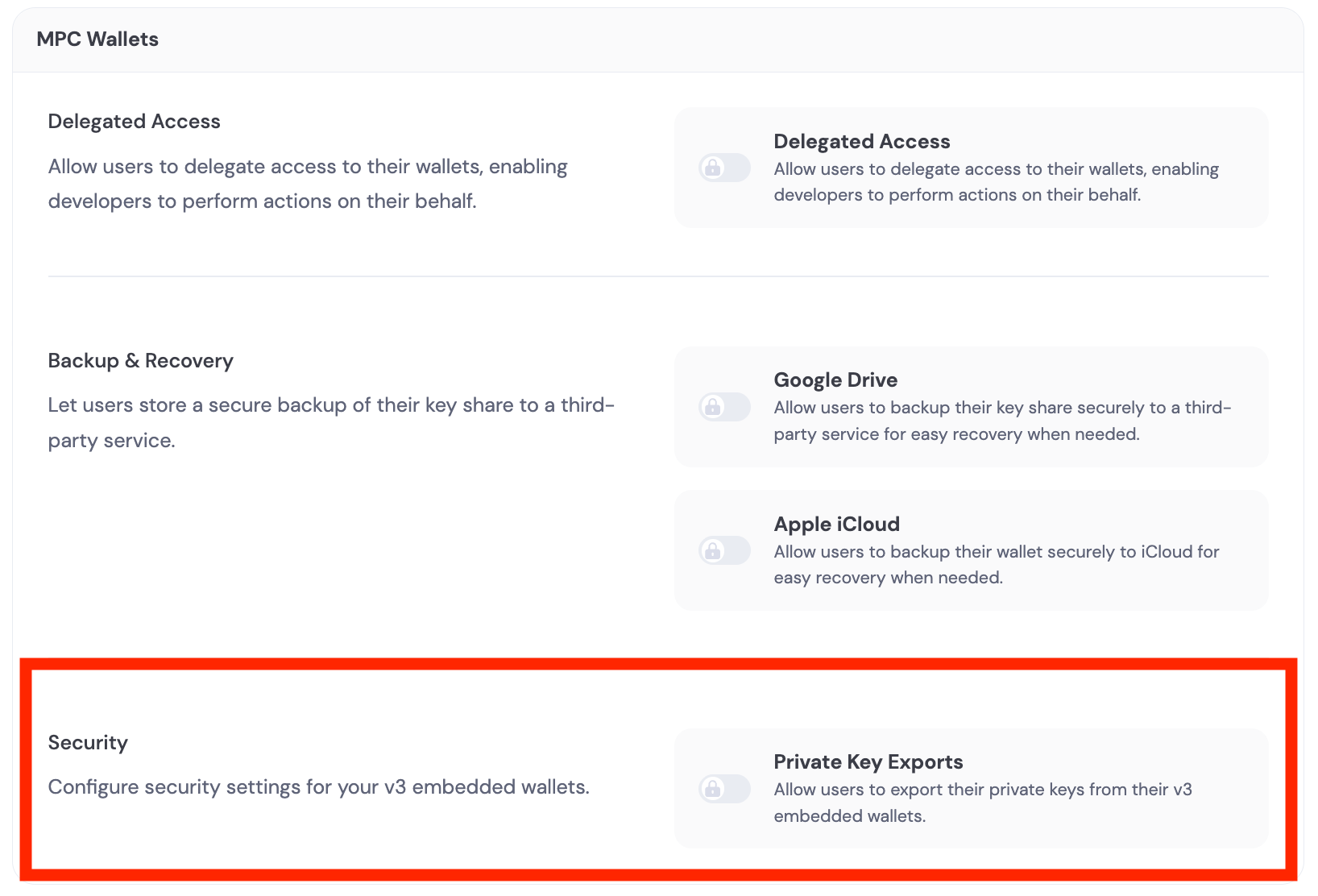
Blocking private key exports
You can disable private key exports for your users via the dashboard. Navigate to Embedded Wallets > MPC Wallets and find the Security section. Toggle off Private Key Exports to prevent users from exporting their private keys.This feature requires the latest SDK version. Make sure to update your SDK before enabling this setting.