Big news! Dynamic is now part of Fireblocks.
Security is our first and top priority
We are SOC 2 Type II and conduct multiple yearly independent code audits. Our TSS-MPC key management ensures top-tier security, with extra levels of protection from advanced MFA options.


TSS-MPC security that scales with you
TSS-MPC provides the ultimate balance of flexibility and security: private keys that are never fully reconstructed, and thresholds that can be adjusted to any use case.
Recent audits
99.9% uptime


July 2025


April 2025


February 2025


September 2024


Ongoing Bounty Program
Flexible MFA for every login and transaction
Protect every step of your user’s journey with an expanded set of tools for added protection.
Learn more
Account-level MFA
Transactional MFA
Enterprise-grade access and controls
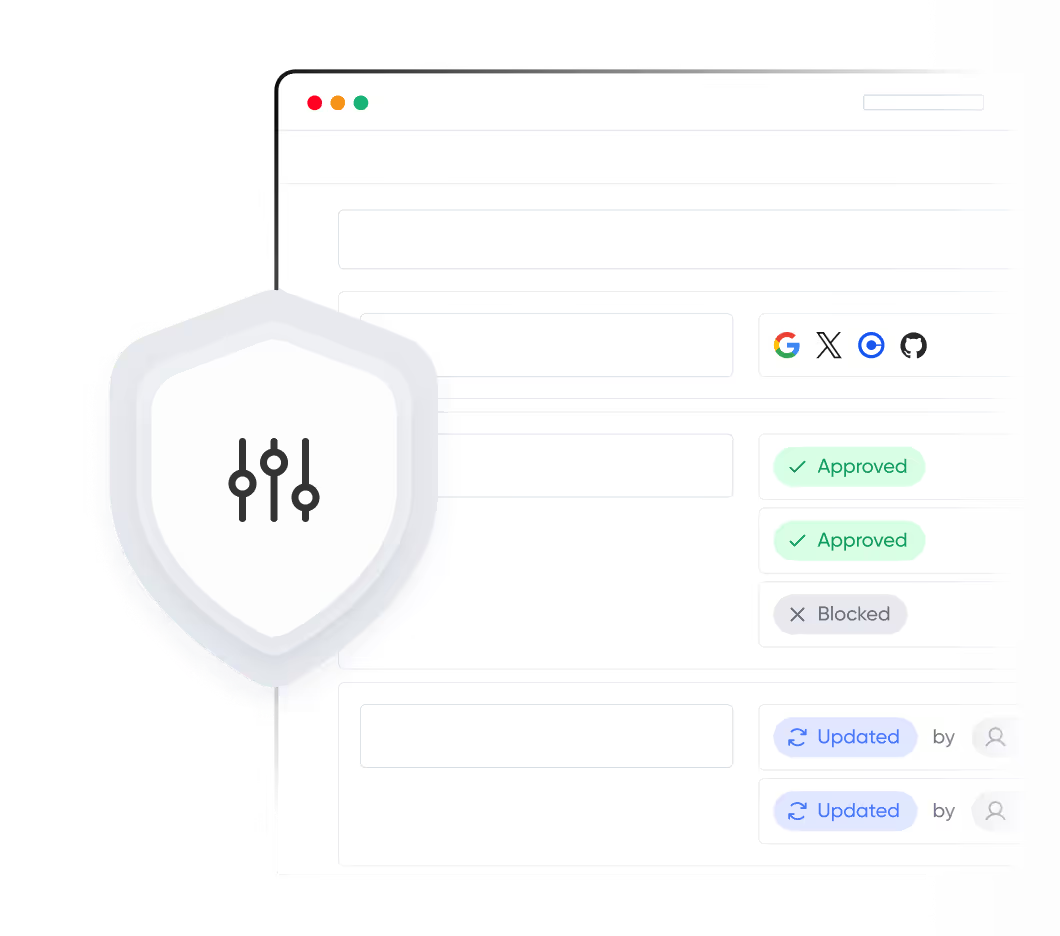
Single Sign-On (SSO)
Securely authenticate users through their existing identity providers, streamlining onboarding while ensuring consistent access and authentication policies.
Scoped API Access
Define exactly which APIs can be used and at what permission level, ensuring least-privilege access that protects sensitive data and developer operations.
Events & Audit Log
Gain full visibility into every action taken across your organization, from developer changes to configuration updates, with a unified audit stream that builds trust.
Learn more
SOC 2 Type II compliant and backed by audits
Being SOC 2 Type II compliant is just the start. We run regular security audits with experts like Cure53, and have active public HackerOne bug bounties in place.
Learn more

What Makes TSS-MPC Different
Discover how Dynamic’s TSS-MPC provides stronger security than Shamir Secret Sharing, legacy MPC, or other approaches that create a full private key.

TSS-MPC
TSS-MPC
Legacy
TSS-MPC
TSS-MPC
Shamir
Secret Sharing
SSS
TEE-Only
Full Private Key
TEE Only
No Single Point of Failure




No Full Key Ever Exists



Reconstructed during signing

Full key exists server side
Distributed Signing




Threshold Support (t-of-n)



More limited than MPC

Reshare Without Keys




Signing Latency

Sub-second signing

5-10 second signing

Moderate

Fast local signing
Key / Account Recovery

If above threshold

If above threshold

If above threshold

Key undecryptable if enclave lost
Regulatory Comfort / Auditability

Easier to reason about distributed trust and non custody

Easier to reason about distributed trust and non custody

Depends on the implementation

Full private key is stored server side
Use of TEEs




Found a potential security issue you'd like us to review?
Squash bugs, score bounties. Help us keep our platform secure through our HackerOne bug bounty program and earn rewards.
Report a bug



