Enterprise Crypto Wallet Security & Key Management: How Leading Teams Stay in Control

Enterprises using crypto operate under a far higher security bar than individual users. Unlike consumer wallets, which protect a single user, enterprise environments involve multiple teams, automated transaction flows, and complex permissioning. Wallets become embedded in treasury management, customer fund flows, and backend systems. That introduces risk across four dimensions: funds, fraud, compliance, and operations.
Enterprises must prove control at every step, not just claim it. Security policies, audit trails, and programmable safeguards have to enforce trust continuously, not after the fact. This requires wallet infrastructure that’s verifiable, automated, and designed for scale, where cryptography and governance work together as part of a cohesive system.
How Different Key Management Models Compare
In modern wallet systems, multi-party computation (MPC) has become the preferred and most secure model for key management. It divides signing authority across multiple participants so that a full private key never exists. Other approaches such as only using Trusted Execution Environments (TEEs) and Shamir Secret Sharing (SSS) trade flexibility for simplicity.
The chart below highlights how these approaches differ in practice.
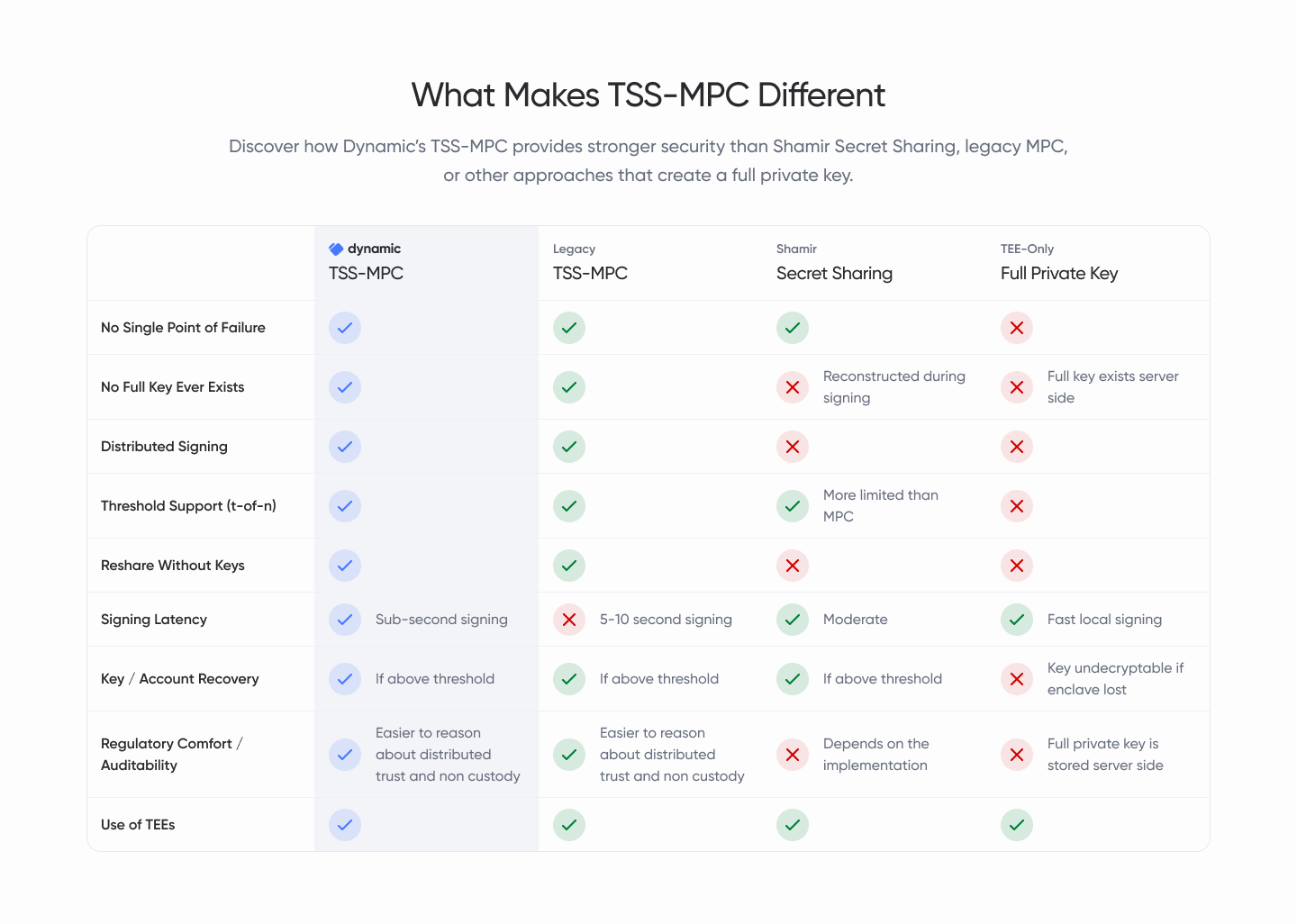
Dynamic uses a threshold-based MPC scheme that continually refreshes key shares and enables secure recovery. It delivers the resilience and verifiability required by regulated institutions while maintaining the performance expected by modern applications.
Certifications That Prove Security
Security programs are only as strong as the standards they meet. Dynamic adheres to certifications and protections including:
- SOC 2 Type II for verified security, availability, and confidentiality controls
- Ongoing bug bounty program backed by HackerOne
- Regular audits from top firms like Trail of Bits and Cure53
These frameworks ensure that Dynamic’s controls are monitored and validated by independent auditors rather than self-assessed claims.
What Enterprises Should Expect from Modern Wallet Architecture
At scale, key management has to be programmable. Security policies should exist in code, not spreadsheets. A production-ready enterprise wallet should include:
- Rotation and refresh of key shares without downtime
- Recovery processes that never construct a full private key
- Policy engines that define spending limits, approval flows, and velocity rules
- Server wallets that allow backend systems to sign transactions safely within defined limits
- Multiple options for additional layers of security such as MFA, Passkeys, and SSO
Dynamic’s wallet infrastructure combines MPC key management with a programmable policy layer so that these safeguards happen automatically within every transaction flow.
Enterprises need to expand digital-asset operations without increasing their risk surface. By pairing verifiable controls with distributed key management, Dynamic makes that possible. The result is custody-grade security designed for applications that operate at internet speed.
FAQs
Why is MPC preferred over TEEs or SSS for enterprise wallets?
MPC distributes signing across multiple parties, removing single points of failure while preserving performance. TEEs depend on one hardware enclave, and SSS requires reconstructing the full key each time a signature is needed.
How does Dynamic verify its security posture?
Through ongoing SOC 2 monitoring, ISO-aligned controls, independent audits, and an active bug-bounty program with HackerOne.
What is a policy engine in wallet infrastructure?
It is a programmable rules layer that enforces approvals, spending limits, and velocity checks before a transaction is signed, ensuring governance at the infrastructure level.
Share this article



