The Future of Wallet Security: Why Dynamic’s TSS-MPC Leads the Pack

Not All Wallet Security Models Are Created Equal
Wallet infrastructure hinges on the security of private keys. For developers, this isn’t just a technical detail, it’s the backbone of user trust. Models such as Shamir Secret Share (SSS) that involve constructing a full private key are often fragile and open private keys to a single point of failure.
This is the same for applications which utilize TEEs but construct a full private key as well. Any approach that reconstructs the full key, even within a "secure" environment, reintroduces a single point of compromise and undermines the resilience of the system.
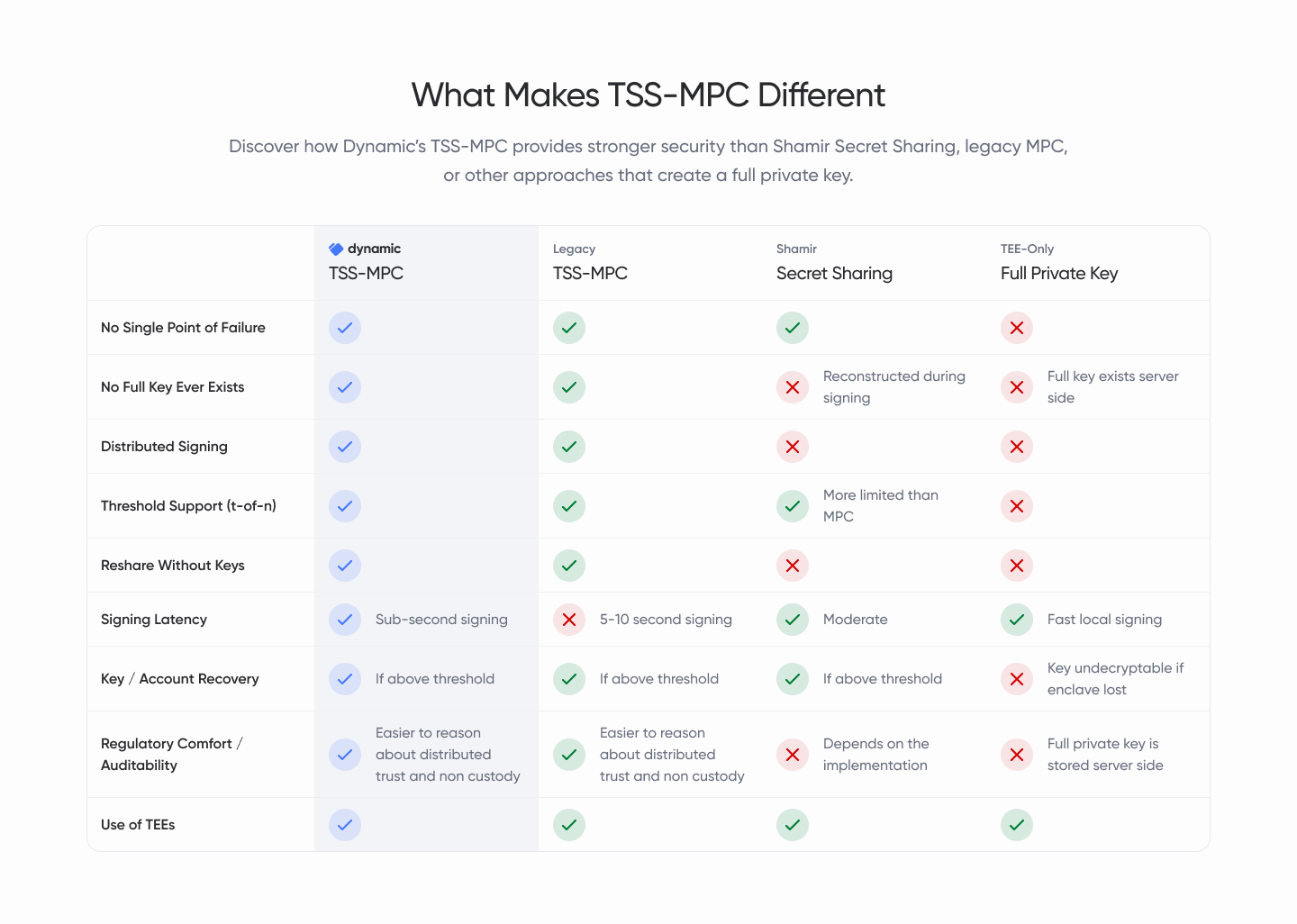
At Dynamic, we’ve implemented an advanced Threshold Signature Scheme based on MPC (TSS-MPC) that blends security, performance, and composability. Before we dive in to the specifics of each category, here’s a matrix that summarizes how Dynamic’s TSS-MPC compares to other popular security models:
No Single Point of Failure (No Full Key Ever Exists)
With TSS-MPC, a full private key never exists, as the key is generated and used in a distributed manner, ensuring no single point of failure. Each key share is held by a different party, and signing requires collaboration across parties. Unlike models that rely on a fully reconstructed key or isolated hardware environments, this significantly reduces the risk of compromise associated with centralized key storage or execution environments.
This cryptographic approach not only minimizes exposure but also eliminates critical dependencies on any one server or hardware module. By distributing trust across multiple parties and enabling secure, real-time collaboration, TSS-MPC offers enhanced resilience against insider threats, infrastructure breaches, and advanced persistent attacks.
Distributed Signing
Dynamic’s model supports fully distributed signing across parties, without centralized coordination. This enables robust multi-operator configurations and allows wallet security to scale with infrastructure. In contrast, Shamir and TEE-only models do not offer true distributed signing, making them more brittle in adversarial conditions.
With distributed signing, key shares remain isolated and active across multiple nodes or operators, enabling fault-tolerant and highly available wallet operations. This model is particularly advantageous for enterprise or protocol-level wallets where uptime, redundancy, and defense against internal compromise are critical.
Threshold Support
Dynamic’s TSS-MPC supports flexible threshold setups, such as 2-of-3 or 3-of-5, enabling highly customizable recovery and signing policies. While Shamir Secret Sharing offers some threshold capabilities, it’s more limited and lacks composability for distributed protocols. TEE-based models typically lack native threshold support altogether.
These flexible threshold configurations allow teams to tailor key management to their specific operational, legal, or governance needs. For example, institutions can require multi-approver signing policies to meet internal compliance standards, while DAOs or cross-border teams can distribute shares across jurisdictions to mitigate regulatory risk.
Key Resharing
Thresholds can also be adapted over time without needing to regenerate the entire key structure. This enables real-time key rotation and enhances long-term security practices by reducing key staleness and exposure risk. This is critical for teams operating in production environments, where downtime or full key regeneration introduces operational risk. Shamir Secret Sharing and TEE-based models lack this capability entirely.
Sub-Second Signing
Dynamic’s TSS-MPC model delivers sub-second signing, making the experience feel fast and responsive for end-users. This is significantly faster than legacy MPC setups, which often take 5–10 seconds per operation. TEE-based systems are fast locally, but they sacrifice resilience by relying on centralized key storage.
Key and Account Recovery
With Dynamic’s TSS-MPC, account recovery is possible as long as the threshold is met. There’s no need for seed phrases or centralized backups. Shamir Secret Sharing offers similar functionality. In contrast, TEE-only systems risk complete key loss if the secure enclave is compromised or lost.
This threshold-based recovery model enables more secure and user-friendly approaches to backup and access control. For example, users or organizations can distribute shares across devices, team members, or recovery agents, ensuring that access can be restored even in the event of device loss or employee turnover. This is especially valuable in environments like custodians, fintech apps, or DAOs, where both security and continuity are essential.
Regulatory Comfort and Auditability
Distributed trust models like Dynamic’s TSS-MPC offer clearer regulatory positioning by avoiding custody and reducing central control. TEE-only models raise concerns, as the full private key is stored on a single server, increasing custodial risk. TSS-MPC also supports transparent access policies and verifiable signing workflows, making it easier to meet audit requirements and align with evolving compliance standards across jurisdictions.
Pairing TSS-MPC with TEEs
While TEEs alone open your platform up to vulnerabilities such as single-point compromise, firmware exploits, or physical access attacks, combining them with TSS-MPC mitigates these risks through distributed trust.
While Dynamic’s model does utilize Trusted Execution Environments (TEEs) for specific operations, it doesn’t rely on them for complete key security. This hybrid approach allows us to benefit from TEE speed without inheriting TEE-only risks.
Dynamic’s modern TSS-MPC implementation was built to meet the needs of today’s apps, wallets, and protocols by offering fast, secure, and programmable key management.
Share this article



